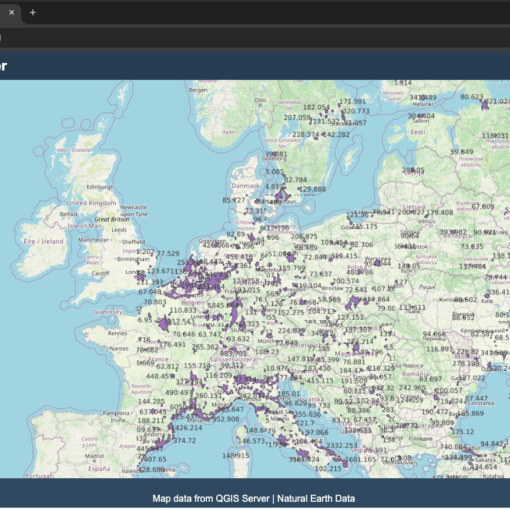
This article shows how to combine QGIS Desktop/Server with Docker Compose and Kubernetes to build scalable geospatial applications. It also covers creating a web client using Angular (or a minimal JavaScript approach), integrating OpenLayers for map rendering, and ensuring all components work seamlessly together.
kubernetes
This article will be a practical one as I intend to showcase a fully automated setup of Keycloak for local testing. However, unlike so many examples out there, this article aims to deploy a production-level Keycloak deployment that uses a Certificate Manager, Sealed Secrets, and PostgreSQL HA (high-availability variant). The goal is to create a development and test environment that behaves as realistically as possible. To make redeployments as easy as possible, we will provide both a single bash script and Helm charts. It’s up to the user to decide which path is more useful. Helm charts are powerful, but […]
This is a follow-up to my previous article on how to setup a Keycloak instance with Postgres on k8s. Surprisingly, it was quite popular on HackerNews and received lots of comments. Among them were questions regarding high-availability and failure resistance. In the original article I described a fairly simple setup running Keycloak and Postgres pods which were accessing manually created PersistenceVolumes and Claims. I showed how to do all that both with handcrafted YAMLs as well as with Helm charts. There is also a repository containing YAMLs and configurations, so before you start working with the solution described here, maybe […]
In this article we will learn how to deploy Keycloak with PostgreSQL on Kubernetes. We will first do everything manually with separate YAMLs and then later with Helm. Our k8s environment will run in Kind, which is an easy to use k8s variant for local expermentation. The sources are located here. Keycloak Keycloak is one of the most popular open-source Identity and Access Management providers. It can run in various environments, from small shops up to giant data centers. Although this article isn’t about IAM’s in general and how to use them, let’s provide a simple definition just to make […]